Developing a Risk-Based Vulnerability Management Program A Real-Life Case Study
Custom Security Solutions Empower Organizations to Create Robust, Efficient Vulnerability Management Programs
Vulnerability management exists for the purpose of identifying and remediating vulnerabilities in systems quickly before they are exploited. Vulnerabilities, which are essentially weaknesses within software can lead to a system or network that can be exploited by attackers. These vulnerabilities must be identified, assessed, and patched regularly to ensure ongoing security. In order to create and maintain a strong security posture, business owners and security officers must be keenly aware of the vulnerabilities on their systems, as well as the process by which they can be quickly patched. If vulnerabilities are not identified or remediated, companies leave themselves open to attacks.
The remediation gap between when organizations first detect vulnerabilities and when those issues are ultimately resolved is on average too long and provides hackers the opportunity to breach systems and organizations. An Adaptiva survey found that companies overwhelmingly do not have adequate staff to manage the number of vulnerabilities and leveraging current vulnerability management tools is a significant cybersecurity challenge. Further, in a study by the Ponemon Institute, 57% of cyberattack victims stated that applying a patch would have prevented the attack. 34% say they knew about the vulnerability before the attack.
The Challenge
A SecureOps client needed security engineers and other security staff to upgrade their vulnerability management program. The state of the program was leaving the client exposed to attacks and had fallen significantly behind industry standards. However, finding a cost-effective solution by leveraging local expertise or traditional managed service solutions were not viable options due to the organization’s need for diverse security expertise, internal control, and visibility to the program and partner flexibility.
The Majority of Security Solution Providers Lack the Flexibility and Staff to Provide the Right Experts at the Right Time
The reality is, as an organization moves up the security maturity curve different types of security experts are required in each stage of the evolution. The vast majority of solution providers are able to provide tactical services to handle scanning, patching, and remediation, but lack the flexibility to provide the right experts at the right time to deliver the right solution.
The Evolution of a Best Practice Vulnerability Management Program
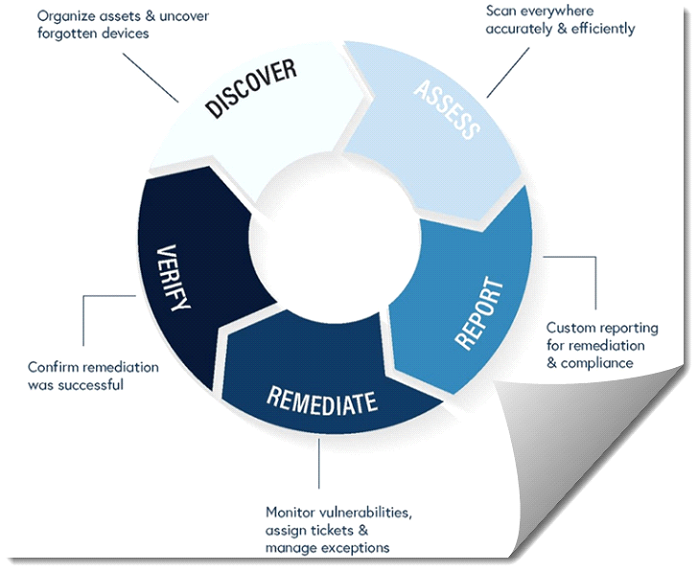
A vulnerability management process consists of five phases:
- Preparation
- Vulnerability scan
- Define remediating actions
- Implement remediating actions
- Rescan
Our client was struggling with a lack of security resources, a fragmented scanning and remediation strategy, and an inefficient reporting and compliance process. Their staff was overwhelmed and had lost faith in the process, tools, and the asset owners who failed to remediate the vulnerabilities that were uncovered. In addition, the organization:
- Scanned less than 50% of the assets each quarter
- Had to manage a high false-positive rate of vulnerabilities due to poor scanner configuration
- Had to conduct ad-hoc scans in order to plug security gaps between quarterly scans
- Had to manually prepare reporting which resulted in an arduous process of pulling together the data
- Had to manage a scan exclusion and exception list that was large and growing
- Could only scan 30,000 IP addresses monthly leaving many assets with critical vulnerabilities
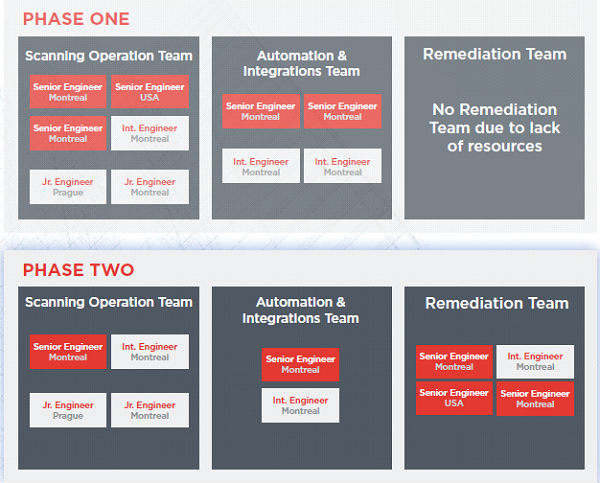
Just to provide some insight into how the IT security team was assembled and organized prior to implementing the risk-based vulnerability management program versus when it was a peak maturity, we provided the organization chart below. The key takeaway is after the program was implemented the organization was able to handle their program with fewer people despite the fact that they were doing far more patching on dozens of additional systems. Further, they were able to finally remediate any vulnerabilities quickly and efficiently.
Key Learning
As organizations move up the security maturity curve, the number of hours they spend on vulnerability scanning, assessments, patching & management decreases. Rather than scanning and patching an entire environment with thousands of systems monthly, risk-based vulnerability management prioritizes high-value systems with a higher level of focus and activity than lower value systems, thus fewer scans, and patches.
The vast majority of an organization’s systems are often of lower value and are not the primary targets for attack yet without a risk-based vulnerability management program they consume the majority of the security team’s time and effort.
The benefit is fewer resources are required to execute the vulnerability management process. Further, they can focus on higher-level responsibilities like remediation, helping threat and incident response teams, asset and vulnerability scoring, and assessing the overall security and business risk level of the organization.
InTandem’s™ Collaborative Model Delivers Customized Expertise, Support, and Personnel
SecureOps’ InTandem™ is a customer-driven solution providing a high-level, diverse, flexible team of experts at the right time with the right skills. Our goal was to provide our client the resources they need to deploy reliable scanning technology, scan their entire environment, and automate their vulnerability management process by prioritizing assets, vulnerabilities, scanning and remediation.
Partnering with our client’s IT security team, SecureOps’ InTandem™ empowered the organization to bolster its vulnerability management program by providing:
- A holistic review of vulnerability management program, requirements, and objectives with recommendations.
- Implementation of a clear, concise vulnerability management strategy geared to bolster overall security maturity.
- The integration of the client’s scanning tools with CMDB platforms and ITSM standards.
- Deployment of new scanners and agents into areas that were unreachable before or where the scans were causing network/firewall issues.
- The handling of all scanning operations to ensure a smooth transition with no adverse effect or loss of current stable state service.
- A large “Discovery Scan” effort to identify areas of the network that had a large number of unmanaged assets, which resulted in improving the accuracy of data in the CMDB.
- Reconfiguration and breaking down of the large scheduled scans into multiple smaller scans to allow custom scanner selection, configuration, policies, frequency, and reporting requirements.
- Creation of a vulnerability remediation and rapid-response team.
Improving security maturity requires dozens of unique, high-level IT security skills delivered by diverse experts. Traditional staff augmentation doesn’t address the evolving needs of their clients
Delivering a Maximum Return on Investment and Improved Security with InTandem™
The benefit of SecureOps’ InTandem™ to our client was the ability to transition from a fragmented, whack-a-mole vulnerability assessment and patching exercise to a comprehensive, prioritized, proactive strategy. The real value of improving the organization’s overall security is by having a partner with specialized experts to implement a best-in-class vulnerability management program.
SecureOps’ InTandem™ enhanced our client’s vulnerability management program by providing measurable results including:
- Risk-based vulnerability management processes were implemented resulting in the evolution of the security program – the high number of resources that were tasked with running basic operations have evolved or been replaced to now perform higher-value functions such as helping asset owners with remediation, supporting Threat and Incident Response teams, performing additional automation and optimization of processes.
- On-demand, costly, inefficient scans are no longer needed.
- The backlog of scans, patching, and remediation was eliminated; vulnerability management is now conducted in near real-time.
- High criticality assets are typically scanned by priority on a daily or weekly basis rather than quarterly.
- Over 20 scheduled scan types are being run across more than 95% of the assets providing more information about system vulnerabilities sooner.
- Scoping and reporting are integrated with ITSM and CMDB, dashboards show a much clearer picture of the vulnerability landscape across the organization.
- Total number of IP scan/rescan monthly: 1,500,000
Prioritizing systems, applications, vulnerabilities by CVSS score, testing patches, and consolidating software versions across an IT environment requires discipline strategies and processes.







